
Managing risk to confidential patient health information (PHI) is not only a critical component of healthcare today; it is also a mandate of the HIPAA Omnibus Rule (HIPAA).
HIPAA mandates that organizations conduct a regular risk analysis to identify and mitigate risks to patient records and the PHI they manage in their electronic health records systems (EHRs). Failure to secure PHI and mitigate the threats and vulnerabilities identified in a risk analysis can result in investigations by the Department of Health and Human Services (HHS) and other federal and state regulatory agencies.
These agencies have authority to impose millions of dollars in penalties and fines as well as extended regulatory oversight, and can do so simultaneously for the same offense.
The Situation
According to the HIPAA Omnibus Rule (HIPAA Omnibus Rule)
1, Failing to protect patient records and prevent disclosure of PHI can damage patients’ financial status, job prospects, and reputation, far exceeding the impact of their medical conditions.
The HIPAA Omnibus Rule requires Covered Entities and Business Associates to conduct regular risk analyses
2 to identify and address threats and vulnerabilities to the confidentiality, integrity and availability of patient records and the PHI they manage and maintain in electronic health information systems.
Millions of dollars in penalties and fines as well as extended regulatory oversight can result from these failures, levied after investigations by the Department of Health and Human Services (HHS) and other federal and state regulatory agencies.
Nearly 30 million patient records have been reported to HHS as compromised in breaches since 2009, according to surveys conducted by healthcare IT security consultants as recently as February 2014[3]. The report states that “(i)n 2013 alone, 199 incidents of breaches of PHI were reported to HHS impacting over 7 million patient records, a 138% increase over 2012.” These statistics do not include breaches that have not been reported to HHS.
Furthermore, HIPAA requires notification of HHS and the patients whose PHI has been breached. Such notification can negatively impact patients’ confidence in as well as the reputation of the service provider. The flip side is that patients build trust in and strengthen their loyalty for their healthcare providers when their PHI is securely managed. A reputation for private and secure management of health information can also serve as a marketing tool for the provider.
In the early roll-out of HIPAA, HHS’ history of lax oversight and few consequences for non-compliance resulted in minimal implementation of the privacy and security standards. Covered Entities lacked comprehensive compliance planning, allocating responsibility over multiple departments to provide workforce training and accountability programs and taking the position that electronic health records systems (EHRs) successfully producing electronic records and bills was sufficient to demonstrate HIPAA and HITECH compliance.
Meanwhile, reports of patient complaints and breaches poured into HHS by the millions. Eighty-three per cent of all large HIPAA privacy and security breaches are the result of theft, according to surveys from HHS sources reported by Healthcare IT News. More specifically, the surveys report that approximately 22% of breaches since 2009 were due to unauthorized access to PHI, 35% were attributed to theft or loss of unencrypted devices containing PHI, and 6% were due to hacking
1.
The results of HITECH’s pilot audit program demonstrated that covered entities lacked understanding of the actual privacy and security standards as well as grounding in the specific implementation requirements the standards impose on internal systems, operations and resources necessary to meet HIPAA compliance requirements.
The HIPAA Omnibus Rule amendments confirm that anything short of a comprehensive, documented and implemented risk management process will not meet HIPAA compliance requirements today. It also requires that risk management program incorporate the results of a comprehensive complaint and breach investigation procedure focused on identifying and addressing workforce errors and patient complaints within the organization. Finally, the HIPAA Omnibus Rule extends these compliance requirements to Business Associates performing services or functions for or on behalf of covered entities.
The Solution
Risk management begins with an organization-wide risk analysis- i.e. an accurate and thorough assessment and mapping out of actual use and disclosure procedures in place for PHI in all formats throughout the whole organization. This includes satellite and multi-state offices, subsidiaries, patient portals, remote access to its PHI/ePHI, and PHI/ePHI disclosed to its Business Associates.
A key component of the assessment involves identifying and planning for mitigation of reasonably anticipated human, natural and environmental threats and vulnerabilities to the organization’s internal and external processes and systems. To be most effective, a risk analysis should be conducted regularly and at key intervals when changes, upgrades and/or mergers take place. The findings from the risk analysis should be incorporated into a document comprehensive and regularly updated risk management strategy for the organization. This documentation is what the OCR will likely request during investigations or audits to evaluate the organization’s compliance efforts.
The next round of OCR audits is scheduled to begin in October 2014. Covered Entities’ and Business Associates’ compliance with the HIPAA security standard’s risk analysis and risk management standard is in the OCR’s cross hairs. Failure to take affirmative steps towards compliance before the OCR comes a’knocking can add additional sanctions for willful neglect to corrective action plans and/or settlement agreements.
Whether the OCR is knocking on your door or not, the private and secure management of the Covered Entity’s or Business Associate’s health information is a critical aspect of quality healthcare services today. Leaders in the industry have this as a critical core value for their organizations, making compliance with the HIPAA Omnibus Rule just par for the course. The availability of secure and reliable healthcare information and data to support quality treatment and services requires the practice of good IT governance and due diligence
2.
Continue reading "Risk Analysis: Prepare Now or Pay Later"
 Our project management courses have been updated to align with the 6th edition of the Project Management Body of Knowledge (PMBOK®) guide. Every course description in the catalog includes a listing of the number of credits by organization. See inset for example of accreditations per course.
Our project management courses have been updated to align with the 6th edition of the Project Management Body of Knowledge (PMBOK®) guide. Every course description in the catalog includes a listing of the number of credits by organization. See inset for example of accreditations per course. Previously, we wrote about how resolving conflict often has the side benefit of building a cooperative bond — even loyalty — between the factions. As each side gains a deeper understanding of the others’ viewpoints, respect builds and morale improves. Cooperative, low stress interactions, create a fertile environment for productive brainstorming, ultimately boosting the health of your organization.
Previously, we wrote about how resolving conflict often has the side benefit of building a cooperative bond — even loyalty — between the factions. As each side gains a deeper understanding of the others’ viewpoints, respect builds and morale improves. Cooperative, low stress interactions, create a fertile environment for productive brainstorming, ultimately boosting the health of your organization. In Part 3 of this series, we’ll examine the five conflict styles that help people understand their own responses as well as diffuse conflict with others. Specifically, we’ll look at the five conflict styles that Kenneth W. Thomas and Ralph H. Kilmann identified and can be assessed in the Thomas-Kilmann Conflict Mode Instrument (TKI), a globally accepted, widely used diagnostic assessment for resolving conflict.
In Part 3 of this series, we’ll examine the five conflict styles that help people understand their own responses as well as diffuse conflict with others. Specifically, we’ll look at the five conflict styles that Kenneth W. Thomas and Ralph H. Kilmann identified and can be assessed in the Thomas-Kilmann Conflict Mode Instrument (TKI), a globally accepted, widely used diagnostic assessment for resolving conflict.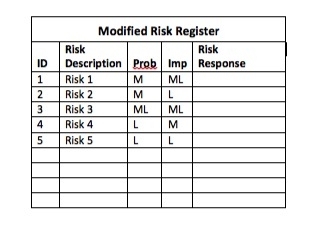 Standard risk responses include Avoidance, Mitigation, Transference, and Acceptance (passive/active). At Merit, we developed a reporting process that would show that the risk factors were decreasing as the project progressed. Supplemented with suitable risk responses, the true reduction of risk probability occurs over time.
Standard risk responses include Avoidance, Mitigation, Transference, and Acceptance (passive/active). At Merit, we developed a reporting process that would show that the risk factors were decreasing as the project progressed. Supplemented with suitable risk responses, the true reduction of risk probability occurs over time. The Probability and Impact Matrix is one of the tools that we recommend in a risk management strategy. It is superimposed with risks that are labeled or numbered as in the above example. “Red” area risks were uniquely documented on a trending month-to-month basis such that it could be seen “driving” toward zero.
The Probability and Impact Matrix is one of the tools that we recommend in a risk management strategy. It is superimposed with risks that are labeled or numbered as in the above example. “Red” area risks were uniquely documented on a trending month-to-month basis such that it could be seen “driving” toward zero.
 May 2014
May 2014 Managing risk to confidential patient health information (PHI) is not only a critical component of healthcare today; it is also a mandate of the HIPAA Omnibus Rule (HIPAA).
Managing risk to confidential patient health information (PHI) is not only a critical component of healthcare today; it is also a mandate of the HIPAA Omnibus Rule (HIPAA).